Newsletter
Subscribe to my newsletter for the latest updates. 👇
By default, any user on a Linux server can use commands like top or htop to view all running processes, including those owned by other users.
While this can be useful in certain situations, it can also pose security risks by exposing sensitive information to potential attackers.
This tutorial shows you how to restrict users from viewing processes owned by other users, thereby enhancing the security of your Linux server.
To make the most of this guide, ensure you have a properly set up Ubuntu server.
If you don’t have one, consider getting a free VPS server to follow along.
Following along on your own server will enhance your understanding and practical experience.
To demonstrate how any user could see processes running by other users, I added a new user named Elie and ran the htop command.
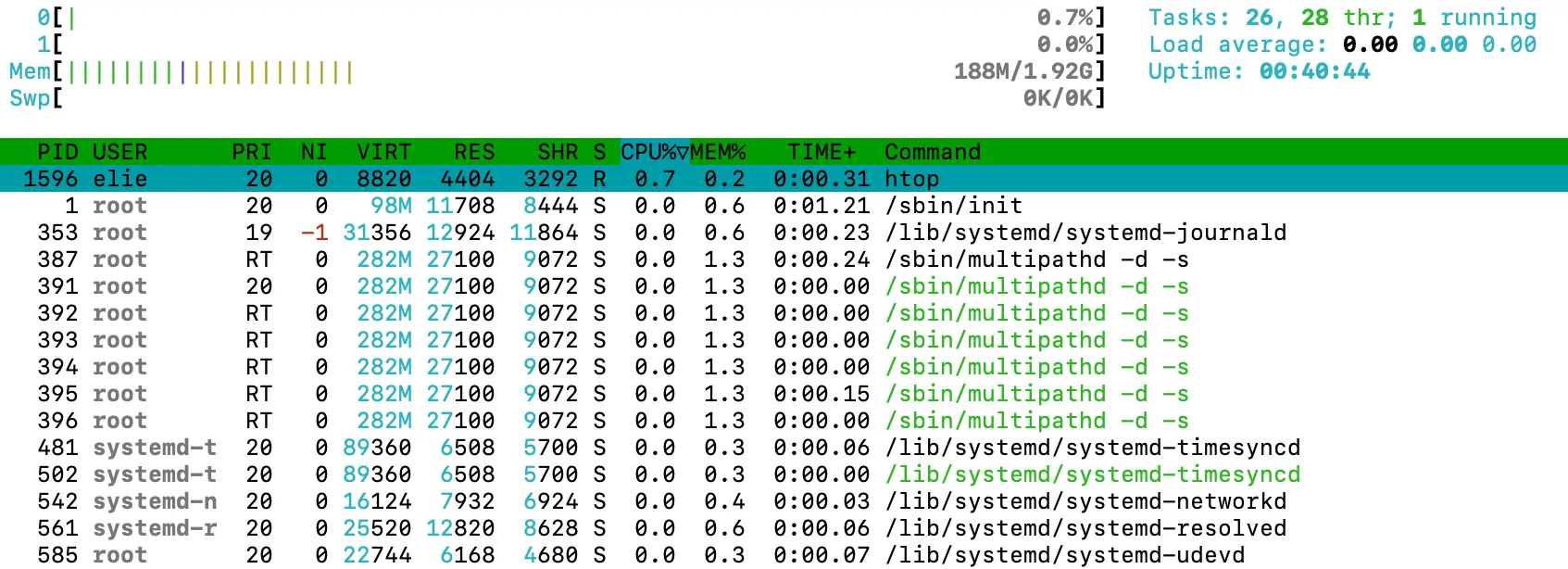
Even with their normal user privileges, Elie is able to see all processes running, including those owned by root and various system users.
To keep users’ processes private, you need to add the following line to the end of the /etc/fstab file:
proc /proc proc hidepid=2 0 0Save and close the file.
Note: This solution doesn’t work for RHEL 9-type distributions. Attempting it may break your server.
Then, remount /proc like this:
sudo mount -o remount procNow, let me switch back to Elie and run the htop command again.
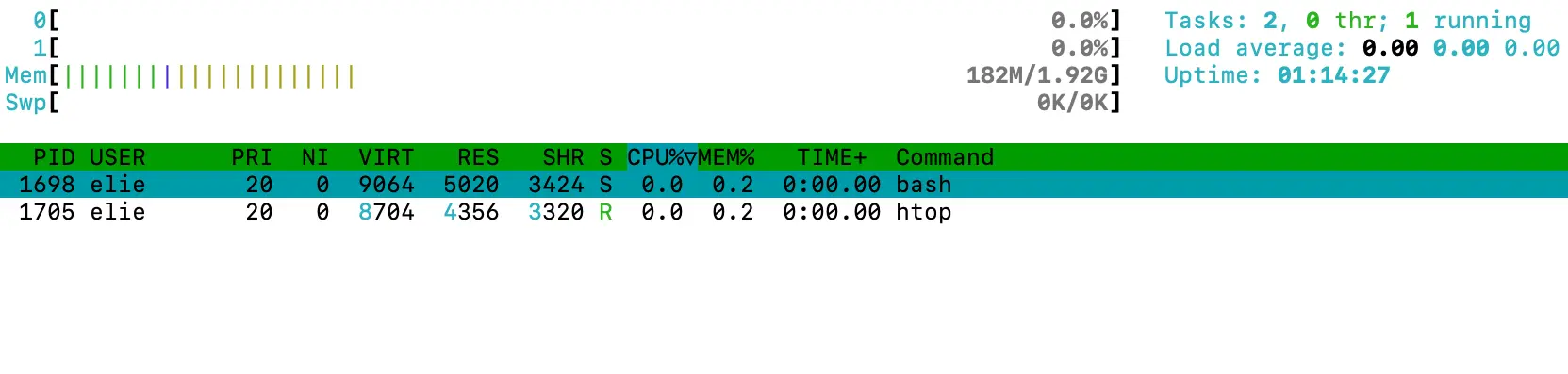
As you can see, Elie is now only able to view their own running processes.
The hidepid option with a value of 2 hides information about all running processes owned by other users, including the process directories in the /proc directory.
Easy, isn’t it?
I hope this tutorial was helpful for you in keeping your users’ running processes private.
However, there’s more to securing Linux servers — advanced measures that I’ve covered comprehensively in my complete server security and hardening guide.
It’s a collection of all security and hardening measures with links to detailed guides for each.
By following these guides one by one, your server will be thoroughly secured.
If you found value in this tutorial or have any questions or feedback, please don’t hesitate to share your thoughts in the comments section below.
Your input is greatly appreciated, and you can also contact me directly if you prefer.